Accton Technology Corp HED2804WBR Barricadeg 2.4GHz 54 Mbps Wireless Router User Manual
Add to my manuals
20 Pages
advertisement
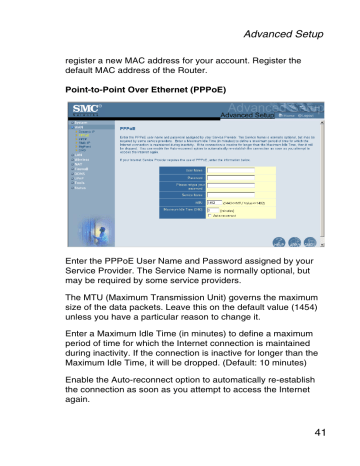
Advanced Setup register a new MAC address for your account. Register the default MAC address of the Router.
Point-to-Point Over Ethernet (PPPoE)
Enter the PPPoE User Name and Password assigned by your
Service Provider. The Service Name is normally optional, but may be required by some service providers.
The MTU (Maximum Transmission Unit) governs the maximum size of the data packets. Leave this on the default value (1454) unless you have a particular reason to change it.
Enter a Maximum Idle Time (in minutes) to define a maximum period of time for which the Internet connection is maintained during inactivity. If the connection is inactive for longer than the
Maximum Idle Time, it will be dropped. (Default: 10 minutes)
Enable the Auto-reconnect option to automatically re-establish the connection as soon as you attempt to access the Internet again.
41
Configuring the Wireless Barricade g Router
Point-to-Point Tunneling Protocol (PPTP)
42
Point-to-Point Tunneling Protocol (PPTP) can be used to join different physical networks using the Internet as an intermediary.
Using the above screen allows client PCs to establish a normal
PPTP session and provides hassle-free configuration of the
PPTP client on each client PC.
Enter the assigned IP address, subnet mask and default gateway
IP address (usually supplied by your ISP), and then the PPTP
User ID, Password and PPPTP Gateway IP address.
Enter a maximum Idle Time Out (in minutes) to define a maximum period of time for which the PPTP connection is maintained during inactivity. If the connection is inactive for longer than the Maximum Idle Time, it will be dropped.
(Default: 10 minutes)
Static IP Address
Advanced Setup
If your Internet Service Provider has assigned a fixed IP address, enter the assigned address and subnet mask for the Router, then enter the gateway address of your ISP.
You may need a fixed address if you want to provide Internet services, such as a web server or FTP server.
43
Configuring the Wireless Barricade g Router
BigPond
44
BigPond is a service provider in Australia that uses a heartbeat system to maintain the Internet connection. Configure the built-in client with your user name, password and service name to get online. Leave the Authentication Service Name as “login-server” for a universal configuration.
DNS
Advanced Setup
Domain Name Servers map numerical IP addresses to the equivalent domain name (e.g., www.smc.com). Your ISP should provide the IP address of one or more domain name servers.
Enter those addresses in this screen.
45
Configuring the Wireless Barricade g Router
LAN
46
• LAN IP – Use the LAN menu to configure the LAN IP address for the Router and to enable the DHCP server for dynamic client address allocation.
• Set a period for the lease time if required. For home networks this may be set to Forever, which means there is no time limit on the IP address lease.
• IP Address Pool – A dynamic IP address range may be specified (192.168.2.2–254). IP addresses running from
192.168.2.100 to 192.168.2.199 are the default value. Once the IP addresses, e.g. 192.168.2.100–199, have been assigned, these IP addresses will be part of the dynamic IP address pool. IP addresses from 192.168.2.2 to 192.168.2.99, and 192.168.2.200 to 192.168.2.254 will be available as static
IP addresses.
Remember not to include the address of the Router in the client address pool. Also remember to configure your client PCs for dynamic IP address allocation.
Advanced Setup
Wireless
To configure the Router as a wireless access point for wireless clients (either stationary or roaming), all you need to do is define the radio channel, the Service Set identifier (SSID), and encryption options.
Channel and SSID
You must specify a common radio channel and SSID (Service
Set ID) to be used by the Router and all of your wireless clients.
Be sure you configure all of your clients to the same values.
ESSID : The Service Set ID. This should be set to the same value as the other wireless devices in your network.
Note: The SSID is case sensitive and can consist of up to 32 alphanumeric characters.
47
Configuring the Wireless Barricade g Router
Transmission Rate : Set the rate of data transmitted from the Router. The lower the data rate, the longer the transmission distance. (Default: Fully Automatic.)
Channel : The radio channel through which the Router communicates with PCs in its BSS. (Default: 6)
Note: The available channel settings are limited by local regulations.
Broadcast SSID: Broadcasting the SSID on the wireless network for easy connection with client PCs.
For security reason, disable SSID broadcast. (Default: Enable)
48
Encryption
Advanced Setup
If you are transmitting sensitive data across wireless channels, you should enable Wired
Equivalent Privacy (WEP) encryption.
Encryption requires you to use the same set of encryption/decryption keys for the Router and all of your wireless clients. You can choose between standard 64-bit or the more robust 128-bit encryption.
You may manually enter the keys or automatically generate encryption keys. To manually configure the keys, enter five hexadecimal pairs for each 64-bit key, or enter 13 pairs for the single 128-bit key. (A hexadecimal digit is a number or letter in the range 0-9 or A-F.) For automatic 64-bit security, enter a passphrase and click Generate. Four keys will be generated (as shown below). Choose a key from the drop-down list or accept the default key. Automatic 128-bit security generates a single key.
49
Configuring the Wireless Barricade g Router
50
If you use encryption, configure the same keys used for the
Router on each of your wireless clients. Note that Wired
Equivalent Privacy (WEP) protects data transmitted between wireless nodes, but does not protect any transmissions over your wired network or over the Internet.
Advanced Setup
NAT - Network Address Translation
From this section you can configure the Address Mapping, Virtual
Server, and Special Application features that provide control over the TCP/UDP port openings in the router’s firewall. This section can be used to support several Internet based applications such as web, E-mail, FTP, and Telnet
Address Mapping
Allows one or more public IP addresses to be shared by multiple internal users. Enter the Public IP address you wish to share into the Global IP field. Enter a range of internal IPs that will share the global IP.
51
Configuring the Wireless Barricade g Router
Virtual Server
52
If you configure the Router as a virtual server, remote users accessing services such as web or FTP at your local site via public IP addresses can be automatically redirected to local servers configured with private IP addresses. In other words, depending on the requested service (TCP/UDP port number), the
Router redirects the external service request to the appropriate server (located at another internal IP address).
For example, if you set Type/Public Port to TCP/80 (HTTP or web) and the Private IP/Port to 192.168.2.2/80, then all HTTP requests from outside users will be transferred to 192.168.2.2 on port 80. Therefore, by just entering the IP Address provided by the ISP, Internet users can access the service they need at the local address to which you redirect them.
The more common TCP service ports include:
HTTP: 80, FTP: 21, Telnet: 23, and POP3: 110
Advanced Setup
Special Applications
Some applications, such as Internet gaming, videoconferencing,
Internet telephony and others, require multiple connections.
These applications cannot work with Network Address
Translation (NAT) enabled. If you need to run applications that require multiple connections, use the following screen to specify the additional public ports to be opened for each application.
Specify the public port number normally associated with an application in the Trigger Port field. Set the protocol type to TCP or UDP, then enter the ports that the application requires.
Popular applications requiring multiple ports are listed in the Popular
Applications field. From the drop-down list, choose the application and then choose a row number to copy this data into.
Note: Choosing a row that already contains data will overwrite the current settings.
53
Configuring the Wireless Barricade g Router
Example:
ID Trigger
Port
1 6112
2 28800
Trigger
Type
UDP
TCP
Public Port Public Type Comment
6112
2300-2400,
47624
UDP
TCP
Battle.net
MSN Game
Zone
For a full list of ports and the services that run on them, see www.iana.org/assignments/port-numbers.
Firewall
The Router firewall can provide access control of connected client PCs, block common hacker attacks, including IP Spoofing,
Land Attack, Ping of Death, IP with zero length, Smurf Attack,
UDP port loopback, Snork Attack, TCP null scan, and TCP SYN flooding. The firewall does not significantly affect system performance, so we advise leaving it enabled to protect your network users.
54
Access Control
Advanced Setup
Using this option allows you to specify different privileges based on IP address for the client PCs.
55
Configuring the Wireless Barricade g Router
Note: Click on Add PC and define the appropriate settings for client PC services (as shown in the following screen).
56
MAC Filtering Table
Advanced Setup
The MAC Filtering feature of the Router allows you to control access to your network for up to 32 clients based on the MAC
(Media Access Control) Address of the client machine. This ID is unique to each network adapter. If the MAC address is listed in the table, that client machine will have access to the network.
57
Configuring the Wireless Barricade g Router
URL Blocking
To configure the URL Blocking feature, use the table below to specify the web sites (www.somesite.com) and/or keywords you want to filter on your network.
To complete this configuration, you will need to create or modify
an access rule in “Access Control” on page 55. To modify an
existing rule, click the Edit option next to the rule you want to modify. To create a new rule, click on the Add PC option.
From the Access Control Add PC section check the option for
“WWW with URL Blocking” in the Client PC Service table to filter out the web sites and keywords specified below.
58
Use the above screen to block access to web sites or to web
URLs containing the keyword specified in the table.
Advanced Setup
Schedule Rule
The Schedule Rule feature allows you to configure specific rules based on Time and Date. These rules can then be used to configure more specific Access Control.
59
Configuring the Wireless Barricade g Router
Enables Schedule-based Internet access control.
1.
Click Add Schedule Rule.
2.
Define the settings for the schedule rule (as shown on the following screen).
3.
Click OK and then click the APPLY button to save your settings.
60
advertisement
* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Related manuals
advertisement